In use case 3, a service is provided by the Service Provider to the Human Service Consumer. Identity info is held at the Identity Provider.
Roles
| Delegation? | No | Yes | ||
| Delegation info PIP | N/A | Service Provider | Entitled Party | Authorisation Reg |
| Auth info 2 PIP: | ||||
| Service Provider | 3 | 3a | 3b | 3c |
Entitled Party | 3.1 | 3a.1 | 3b.1 | 3b.1 |
| Authorisation Reg | 3.2 | 3a.2 | 3b.2 | 3b.2 |
| Identity Provider* | 3.3 | 3a.3 | 3b.3 | 3c.3 |
As there is no delegation, the Entitled Party acts as Human Service Consumer
Depiction
Description
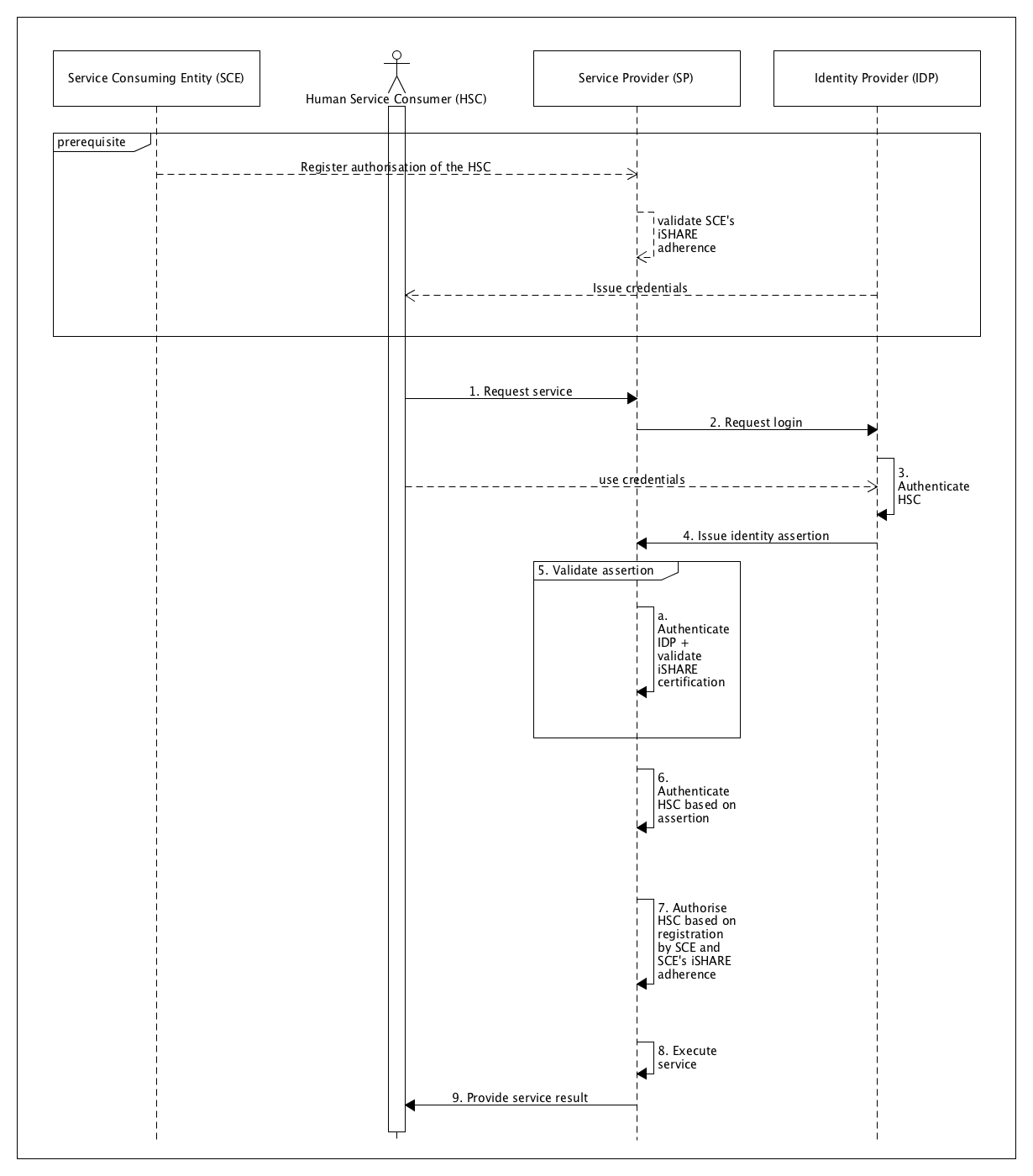
It is prerequisite of this use case that:
- The Service Provider has and manages its own authorisation information indicating what Entitled Parties are entitled to what (parts of) services*
- The Entitled Party has and manages its own authorisation information indicating which Human Service Consumers are authorised to act on its behalf**
- The Entitled Party registers the authorisation information at the Service Provider
- The Human Service Consumer is able to authenticate the Service Provider
- The Service Provider is able to authenticate the Human Service Consumer
- The Identity Provider is able to authenticate the Service Provider
- The Service Provider is able to authenticate the Identity Provider
- The Human Service Consumer has been issued identity credentials by the Identity Provider
- In this use case the Entitled Party acts as Human Service Consumer
* The Service Provider can outsource this function to a third party
** The Entitled Party can outsource this function to a third party
The use case consists of the following steps:
- The Human Service Consumer requests a service from the Service Provider
- The Service Provider requests a login from the Identity Provider
- The Identity Provider authenticates the Human Service Consumer
- The Identity Provider issues an identity assertion to the Service Provider
- The Service Provider validates the identity assertion through the following steps:
- The Service Provider authenticates the Identity Provider and validates it as an iSHARE certified party
- The Service Provider authenticates the Human Service Consumer based on the validity of the identity assertion
- The Service Provider authorises the Human Service Consumer based on the authorisation information registered with the Service Provider
- The Service Provider executes the requested service
- The Service Provider provides the service result to the Service Consumer
Practical examples
All Functional working group-members are invited to add practical examples of this use case in the comment section.