...
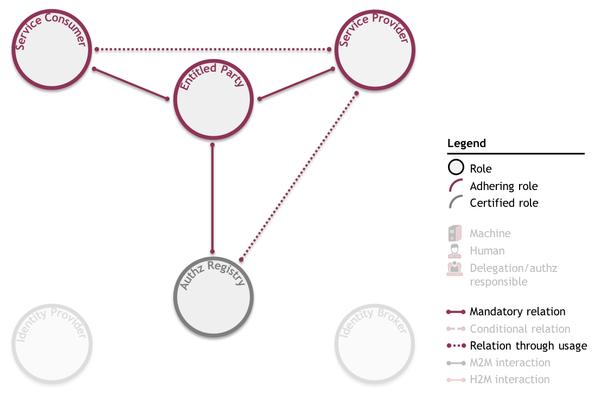
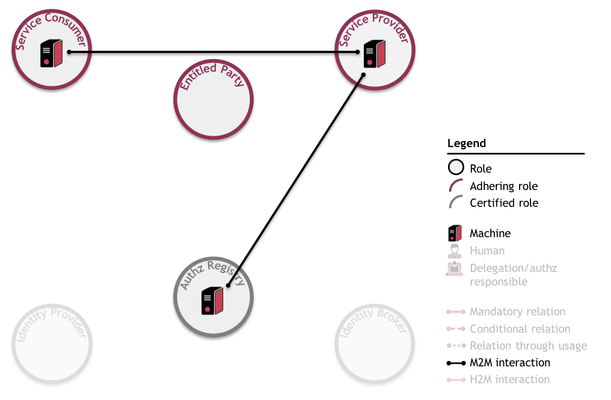
- As always, a mandatory relation between the Entitled Party (Party A) and the Service Provider (Party C) establishes the entitlements of the Entitled Party (Party A);
- A mandatory relation between the Entitled Party (Party A) and the Service Consumer (Trucking Company B) covers the delegation of the right to request a time slot;
- A mandatory relation between the Entitled Party (Party A) and the Authorization Registry (D) covers the outsourcing of managing delegation information.
- No relation between the Service Consumer (Trucking Company B) and the Service Provider (Party C) is mandatory before service consumption, i.e. the Service Consumer and the Service Provider do not need to know each other. This relation only commences through usage;
- No relation between the Service Provider (Party C) and the Authorization Registry (D) is mandatory before communication. This relation also commences through usage.
As depicted:
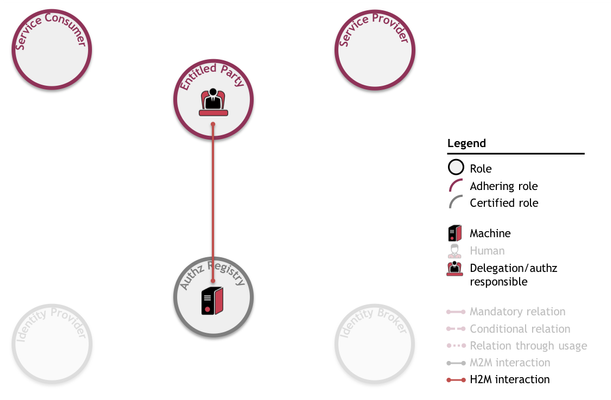
Prerequisites
...
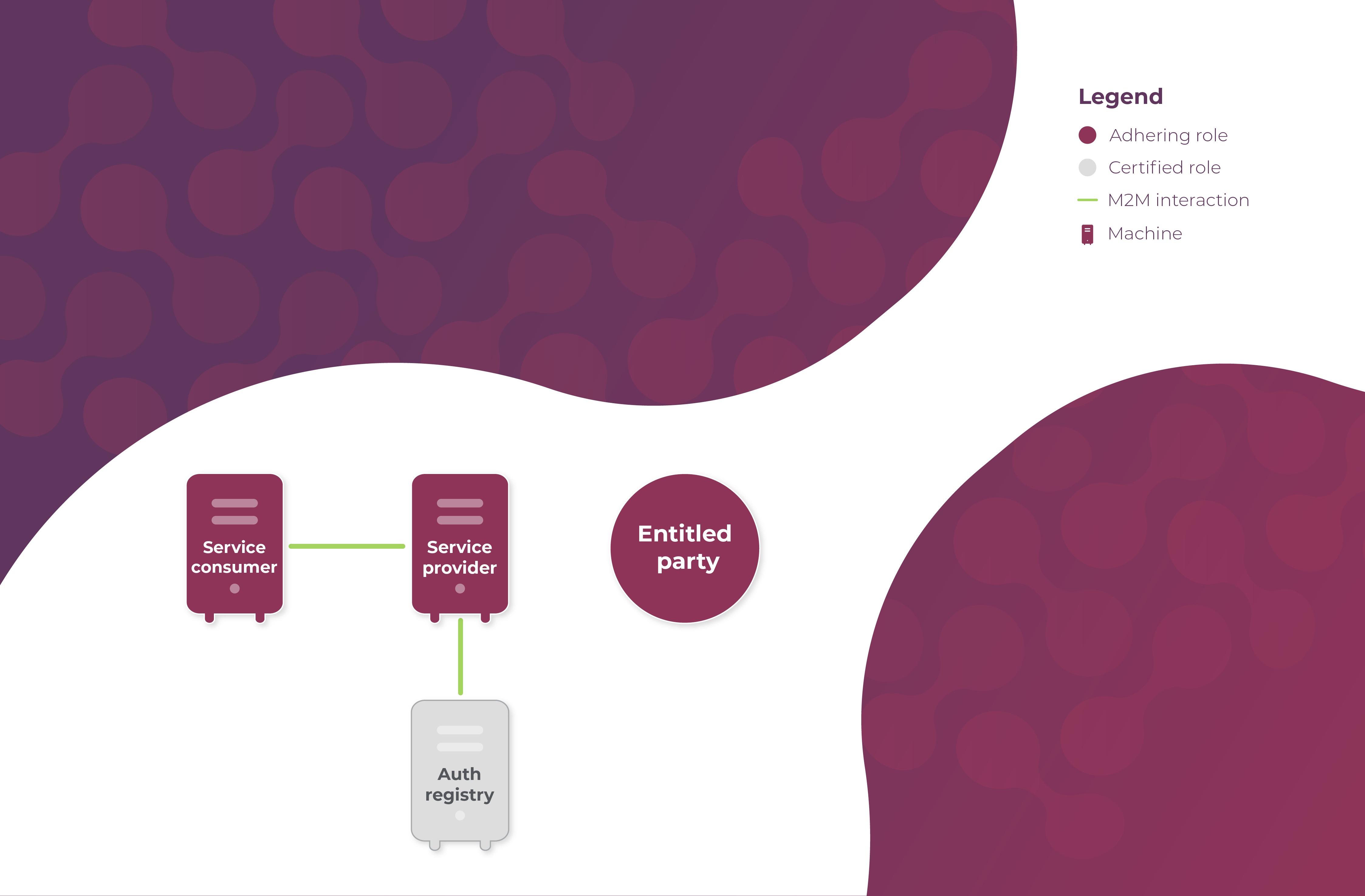
The prerequisites in bold are depicted as follows:
Use case
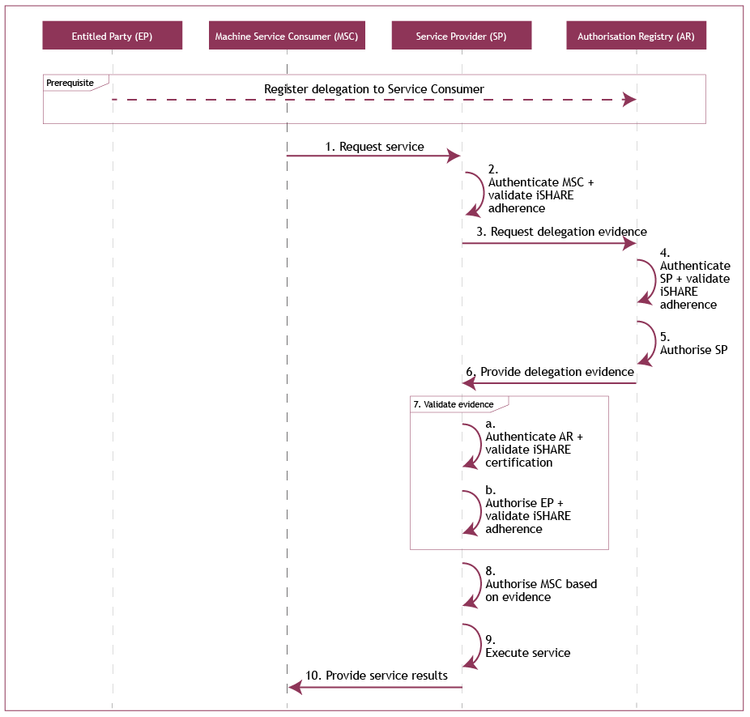
The use case consists of the following steps:
- The Machine Service Consumer (of Trucking Company B) requests a service from the Service Provider (Party C);
The Service Provider (Party C) authenticates the Machine Service Consumer (of Trucking Company B) and validates the iSHARE adherence of the Service Consumer (Trucking Company B);
- The Service Provider (Party C) requests delegation evidence from the Authorization Registry (D);
- The Authorization Registry (D) authenticates the Service Provider (Party C) and validates its iSHARE adherence;
- The Authorization Registry (D) authorizes the Service Provider (Party C) based on the scheme agreements for providing delegation information;
- The Authorization Registry (D) provides the delegation evidence;
- The Service Provider (Party C) validates the received delegation evidence through the following steps:
- The Service Provider (Party C) authenticates the Authorization Registry (D) and validates its iSHARE certification;
- The Service Provider (Party C) authorizes the Entitled Party (Party A) based on the entitlement information registered with the Service Provider (Party C), and validates its iSHARE adherence.
- The Service Provider (Party C) authorizes the Machine Service Consumer of the Service Consumer (Trucking Company B) based on the validity of the delegation evidence;
- The Service Provider (Party C) executes the requested service;
- The Service Provider (Party C) provides the service result to the Machine Service Consumer (of Trucking Company B).
As depicted:
Note that this use case is exactly the same as derived use case 1c, as found under detailed Functional descriptions. This section also includes delegation use cases with delegation information held by other roles than an Authorization Registry.
Sequence diagram
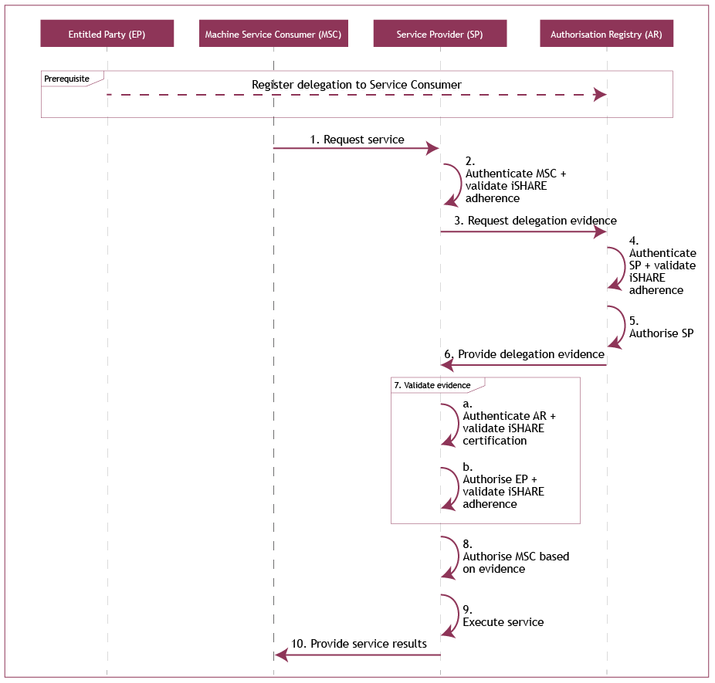
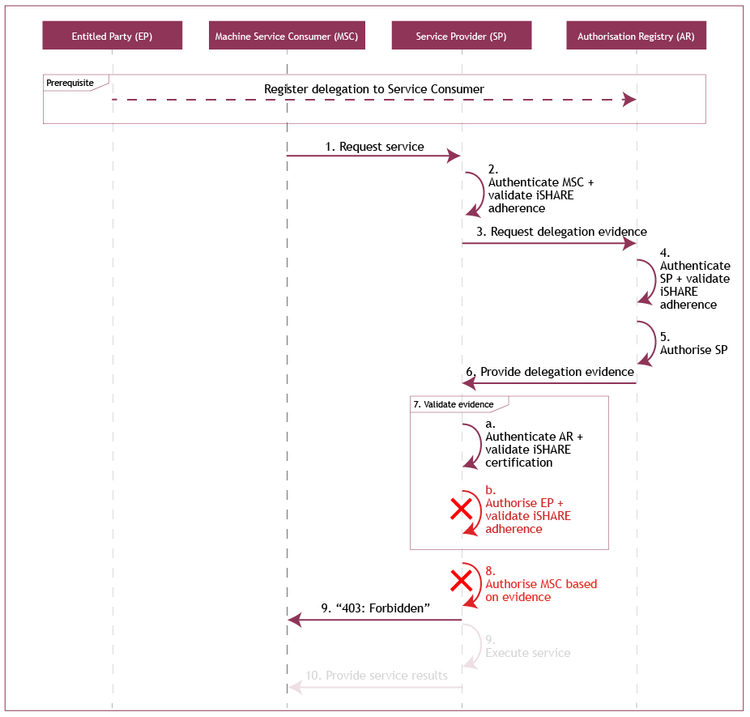
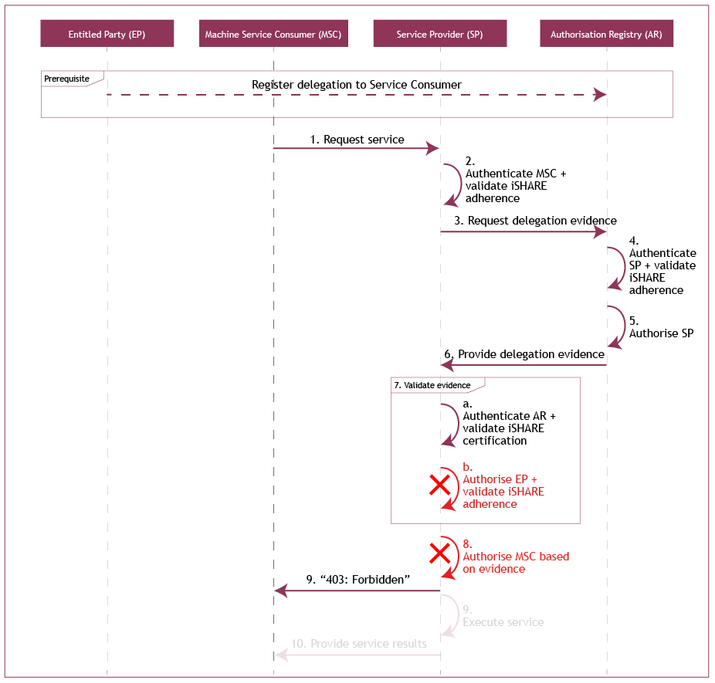
Alternative scenario on management of consent
...
- The Machine Service Consumer (of Trucking Company B) requests a service from the Service Provider (Party C);
The Service Provider (Party C) authenticates the Machine Service Consumer (of Trucking Company B) and validates the iSHARE adherence of the Service Consumer (Trucking Company B);
- The Service Provider (Party C) requests delegation evidence from the Authorization Registry (D);
- The Authorization Registry (D) authenticates the Service Provider (Party C) and validates its iSHARE adherence;
- The Authorization Registry (D) authorizes the Service Provider (Party C) based on the scheme agreements for providing delegation information;
- The Authorization Registry (D) provides the delegation evidence;
- The Service Provider (Party C) validates the received delegation evidence through the following steps:
- The Service Provider (Party C) authenticates the Authorization Registry (D) and validates its iSHARE certification;
- The Service Provider (Party C) CANNOT authorize the Entitled Party (Party A) based on the entitlement information registered with the Service Provider (Party C)
- The Service Provider (Party C) CANNOT authorize the Machine Service Consumer of the Service Consumer (Trucking Company B) based on the validity of the delegation evidence;
- The Service Provider (Party C) communicates an access forbidden message to the Machine Service Consumer (of Trucking Company B).
Sequence diagram
What needs to be implemented technically for this use case (and the alternative scenario) is described generically, and specifically per role in the iSHARE Developer Portal.